
Cyber Physical Systems Security – Why the Cyber Element is Key
Cyber-physical systems are robots by another name. The “brain” of every robot is a computer, and all computers can be hacked and compromised. And because of the physical dimensions in play, cyber physical systems security is a high stakes challenge. Hacked robots can pose a clear and present danger when compared to a simple cyber system, such as a laptop with personal data.
Losing your personal data to some unscrupulous actor can leave you in a metaphorical world of hurt – but losing control of your robot can leave many people in a literal world of pain. Imagine a war scenario where an adversary takes control of self-driving vehicles to terrorize motorists and pedestrians. (This has been demonstrated, in simulation, with both Jeep and GM cars.) The same state actor could take over manufacturing robots on a nationally strategic production line to cripple the logistical supply line.
Most commonly, robotics attacks are focused on spoofing sensor input, causing the robotic system to go awry.
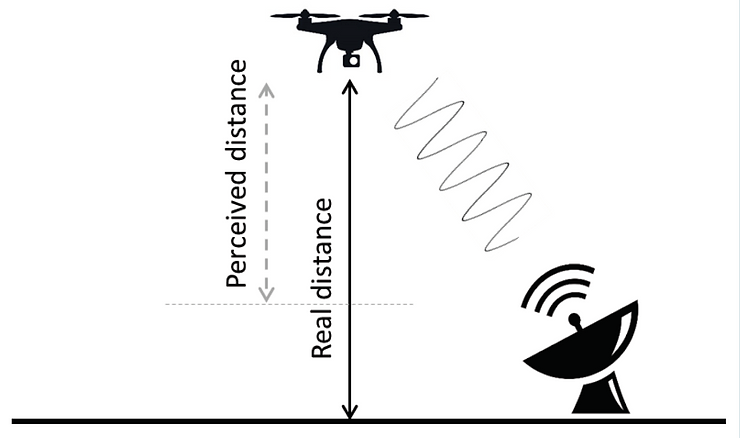
Image taken from this paper on ultrasonic spoofing attacks for UAVs.
An example of how such a spoofing attack works on autonomous vehicles can be found here.
The takeaway? When it comes to cyber physical systems security, the cyber dimension is critical; quite literally a matter of life and death. The good news is that there are established practices for securing cyber systems – from NIST (The National Institute of Standards and Technology), for example. Securing robots is simply an application of existing cybersecurity practices.
How Security is Integral to Safety
Cybersecurity refers to the protection of computer systems, networks, and data from unauthorized access, damage, or theft. In the context of a cyber-kinetic system, which involves a physical entity controlled by software and connected to the internet or other networks, the need for robust cybersecurity becomes even more critical: Security is integral to safety because it provides the necessary measures to protect against potential threats, vulnerabilities, and risks that can compromise the well-being of individuals, systems, or assets.
In the context of a cyber-kinetic system like a robot, security measures play a crucial role in ensuring the overall safety of the system and its interactions with the environment and users. Here’s how security directly impacts safety:
- Preventing Unauthorized Access: Security measures like authentication and access controls prevent unauthorized users from gaining control over the robot.
- Detecting and Mitigating Threats: Early detection allows for timely responses, including isolating the system from the network or shutting it down if necessary, to prevent harm.
- Data Protection: Cyber-kinetic systems often process and store sensitive data, including user information and operational data. Robust security practices, such as encryption and data access controls, safeguard this information from unauthorized access, reducing the risk of privacy breaches and identity theft.
- Ensuring System Integrity: Security measures verify the integrity of the system’s software and firmware, ensuring that it has not been tampered with or modified by unauthorized parties. This helps maintain the robot’s intended behavior, reducing the likelihood of unpredictable or unsafe actions.
- Securing Communication: Many cyber-kinetic systems rely on network communication to function and receive commands. Implementing secure communication protocols helps prevent unauthorized parties from intercepting and sending malicious commands to the robot.
- Safe Remote Operations: In scenarios where robots are operated remotely, strong security measures are essential to protect the communication channel and prevent unauthorized access.
Layers of Security for Robots
Cyber physical systems security involves measures to protect the confidentiality, integrity, and availability of data that the robot collects, processes, or stores. It encompasses various safeguards to prevent unauthorized access, data breaches, or tampering with sensitive information. Broadly, there are five layers of security:
- Physical access: Limiting who or what can physically reach the robot; in a co-bot setting, where robots interact with humans to make them more efficient, access should be limited to those who actively use the robots and the proper engineering and maintenance crew. A good rule of thumb is to have a least-privileged access model in a physical setting.
- Network access: Just like its physical counterpart, network access must follow the least-privileged model by setting up access controls that limit who can access specific subsystems or data within the robot. Proper authentication and authorization mechanisms ensure that only authorized users can access the robot at the right levels. Furthermore, employing secure communication protocols ensures that data transmitted between the robot and other systems, such as control centers or cloud servers, is protected from eavesdropping and tampering.
- End-point security: If the robot interacts with external systems or users through application programming interfaces (APIs) or other interfaces, ensuring their security is crucial to prevent unauthorized access and data exposure. Implementing regular data backups ensures that valuable data can be recovered in case of data loss or a security incident. This helps prevent permanent data loss and enhances the system’s resilience.
- Application security: Regularly assessing the robot’s software and firmware for vulnerabilities and promptly applying security patches and updates helps prevent exploitation of known weaknesses. Furthermore, Data integrity checks verify that the data remains unaltered and accurate throughout its lifecycle. This involves using cryptographic hashing and checksums to detect any unauthorized modifications or data corruption.
- Data security: Data security involves secure data storage practices, including encryption of data at rest, to protect information stored on the robot’s onboard memory or external storage devices. Implementing data encryption ensures that any data transmitted or stored by the robot is scrambled and can only be deciphered with the appropriate encryption key. This prevents unauthorized parties from understanding the data even if they manage to intercept it. Furthermore, when possible, sensitive data can be anonymized or pseudonymized to protect individual privacy. Anonymization removes personally identifiable information, while pseudonymization replaces identifying elements with artificial identifiers.
Best Practices for Cyber-Physical System Safety
In addition to the key layers of security discussed above, implementing the following best practices for cyber physical systems security is essential to mitigate risks and ensure the reliable and secure operation of robots. Think of these best practices guidelines as operational protocols:
- Thorough Risk Assessment: Conduct a comprehensive risk assessment to identify potential threats, vulnerabilities, and hazards that could impact the CPS. Understanding the risks helps in prioritizing safety measures and allocating resources effectively.
- Understand the software bill of materials: What is in the code and who wrote them? Admittedly, this is a difficult task in the open source era with indiscriminate software pulls that deliver lots of (wanted and unwanted) functionality, but there are a set of innovative startups specializing on solving this problem.
- Security by Design: Implement security measures from the initial design phase of the CPS. Security considerations should be an integral part of the system architecture and not an afterthought. Use encrypted and authenticated communication protocols to protect data exchanged between CPS components and external systems.
- Defense in Depth: Employ multiple layers of defense to protect the CPS from cyber and physical threats. This includes a combination of firewalls, access controls, encryption, intrusion detection systems, and physical security measures.
- Least Privilege Principle: Follow the principle of least privilege, granting only the minimum level of access required for each user, process, or component to perform its designated function. Use strong access control mechanisms, such as multi-factor authentication, to ensure that only authorized personnel can access and interact with the CPS.
- Testing and Validation: Conduct rigorous testing and validation procedures to ensure that the CPS meets safety standards and performs as expected under various conditions.
- Continuous Monitoring: Implement real-time monitoring of the CPS to detect anomalies, security breaches, or performance issues promptly. Automated alerts and incident response plans should be in place. Ensure that all software and firmware components of the CPS are regularly updated with the latest security patches to address known vulnerabilities.
- Built in safety-triggers: Incorporate redundancy and fail-safe mechanisms to prevent single points of failure and provide backup systems in case of emergencies or malfunctions.Emergency stops arrest the robotic system when all else fails.
- User Training and Awareness: Train all users and personnel involved in the operation and maintenance of the CPS about safety practices, security protocols, and potential risks. Adhere to industry-specific safety and security standards and regulations relevant to the CPS deployment. Regularly assess and update the CPS’s safety measures and security protocols as technology evolves and new threats emerge.
- Incident Response and Recovery Plan: Have a well-defined incident response plan in place to handle security breaches or safety incidents promptly. This plan should include recovery procedures to restore the CPS to a secure state.
By incorporating these best practices, organizations can enhance the safety and security of their cyber-physical Systems, minimize the potential for cyber-physical attacks, and ensure the reliable and safe operation of these critical systems.
Never Take Shortcuts
Cyber physical systems security must be built into the robotics design starting the design stage. Security and safety are best when baked into the design from day one. And, done correctly, there is no performance compromise when delivering secure and safe solutions to the world.
We, at 3Laws, provide important software services for robotics companies, ranging from a developer diagnostics dashboard, to a support diagnostics dashboard, to inherent and certifiable safe robotic operations in the field. When we render our services to you, we take the above guidelines into account to assure that we enhance security and safety. However, we are only a part of the broader solution that you are making for your market. Please be mindful of your cybersecurity practices as you deploy your cyber-kinetic systems in the real world.
Leveraging the best cybersecurity is an ideal starting point. And, ultimately, it translates to robotics safety. Nobody wants to see a real-life version of Maximum Overdrive.